Introduction
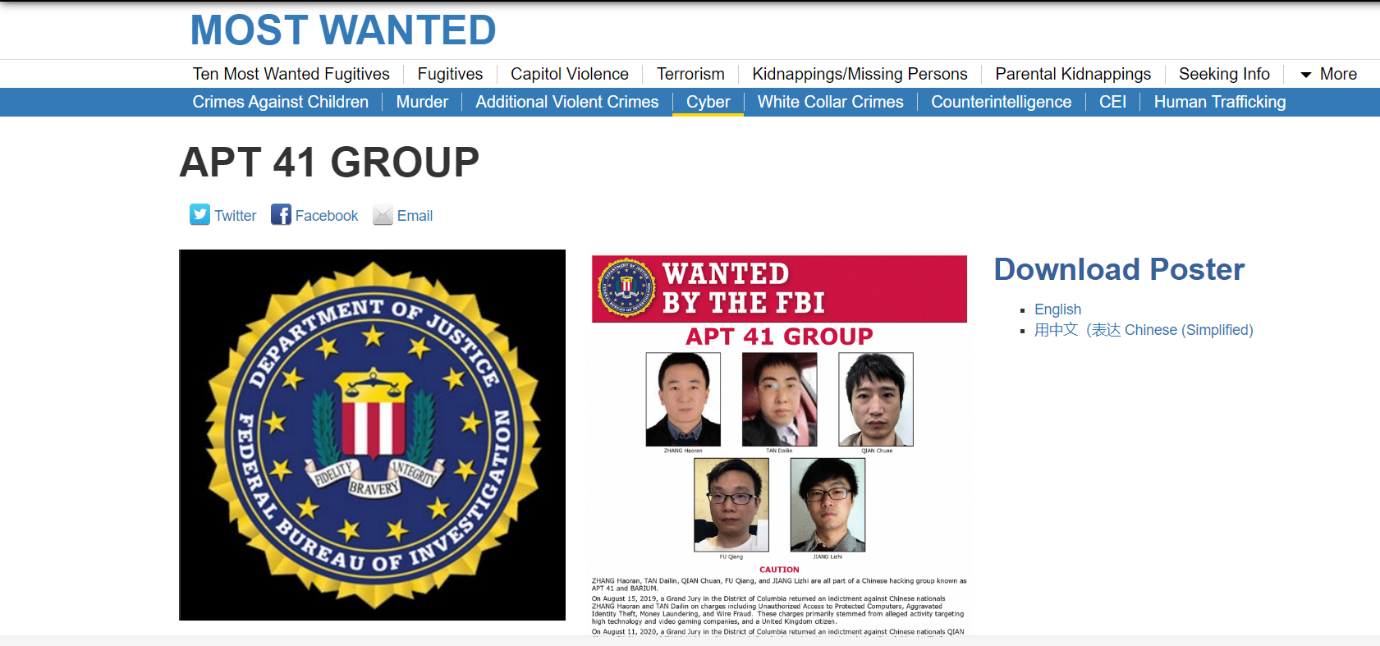
ATP -41, popularly known as HOODO or Advance Persistent threat41, is a cyber espionage group that is believed to be associated with the Chinese government. The group has been Active since 2012 and has been targeting various organisations such as healthcare, technology, and telecommunication, including government and private agencies globally. Recently, ATP-41 was in the news, as it was caught spying on Google open-source GC2(Google Command and Control) for a data theft Attack. In this blog post, we will learn more about ATP-41 and its attacks.
Back Drop
ATP -41, popularly known as HOODO or Advance Persistent threat41, is a cyber espionage group believed to be associated with the Chinese government. The group has been actively working since 2012, FBI 2020 issued a lookout notice in the year 2020 for its members. The group was charged with racketeering, money laundering, fraud, identity theft, and access device fraud on August 11, 2020. These allegations originate from their claimed unauthorised computer intrusions while working for Chengdu 404 Network Technology Company. The defendants allegedly launched supply chain attacks to acquire unauthorised access to networks worldwide, targeting hundreds of firms from various industries such as social media, telecommunications, government, defence, education, and manufacturing. Companies from Australia, Brazil, Germany, India, Japan, and Sweden were among the casualties. The defendants reportedly went after telecom companies in the United States, Australia, China (Tibet), Chile, India, Indonesia, Malaysia, Pakistan, Singapore, South Korea, Taiwan, and Thailand. The accused allegedly carried out attacks with ransomware and dictated payments from victims. This group has recently targeted the videogame industry and British citizens as well.
How does ATP-41 Attack happen?
As the Investigation against ATP-41 is in process, it is difficult to publicly share the entire details because of its sensitive nature. However, based on the prior attacks, it is likely that the attackers deploy advanced means to the targeted systems, such as social engineering, malware or other Sophisticated techniques.
Another possible method of attack is through phishing attacks emails to the victims, where the attackers send an email that seems to be legitimate with a malicious attachment or link that, when opened or clicked, installs malware on the victim’s computer or laptop. Once the attackers gain access to use the victim’s system, they may use various techniques to expand their reach, such as lateral movement, privilege escalation, and Exploiting weaknesses in software or hardware utilised by the targeted organisation is another possibility. To access a victim’s machine, the attackers may use a vulnerability in a popular software program or target a specific hardware component to exploit a weakness.
It’s also possible that the attackers used these methods to obtain access to the systems under assault. Whatever approach was employed, the ATP41 cyber assault emphasises the significance of having strong cybersecurity measures and always being watchful against future attacks.
Impact and Upshot of ATP-41 Cyber Attack
The impact of a Cyberattack on organisations and big tech giants could be significant. A successful cyber-attack on any organisation could result in theft, financial fraud, and other cyber crimes. Additionally, this could result in the loss of trust and reputation for the company, which could lead to a decline in the number of users and effects the financial performance. It could also lead to legal and regulatory consequences.
Responses and Recovery Efforts: – the following steps can be involved in the response and recovery of a cyber Attack these are as follows:
- Containment: The Initial step is to confine the attack and prevent additional damage. This may include isolating or modifying systems, restricting network access, or preventing the attacks from expanding their influence.
- Investigate: the next step is to study the attack to a particular nature and the amount of damage. Forensic analysis, data recovery, and other approaches may be used to identify the attackers and their tricks.
- Remediation: Eventually, the attacks have been controlled and examined, and the next step is to repair the damage. This might include restoring the impacted system and fixing vulnerabilities.
- Communication: informing each impacted party, including stakeholders and users, about the incident is crucial. The communication should be honest, timely, and in a clear and transparent manner.
- Prevention: the final step is to identify the variabilities and fix them apart from them, tighten the security controls, train the employees, and create cyber awareness among them.
The response and recovery depend on the preparedness and response capabilities of the organisation.
Conclusion
The lessons learned from the attack are essential for the future as many cybercriminals might try and replicate such attacks with different intensities. We must create awareness of such attacks and encourage active netizen participation to address the crime. The platforms, in synergy with the CSOs and Govt, can create a blanket of protection by incorporating emerging technology tools to overcome and prevent such attacks resulting in massive financial and data loss.
Author : Ms. Tanushree Saxena, Trainer, CyberPeace